This post How to Protect Your Money from Financial Warfare appeared first on Daily Reckoning.
There are many bad actors out there who are preparing to inflict as much damage as possible to the power grid and other critical infrastructure, including the stock market.
I would put Russia, China, Iran, North Korea and a few others at the top of the list. Russia and China at the top of the list but Iran certainly has good cyber-warfare capability.
They’re employing what they call Cyber Brigades that spend all their time basically hacking into the critical infrastructure systems I described above. It’s a good bet that all of these systems have already been penetrated.
No one can beat the U.S. in a conventional war right now. China, especially, is catching up, but it’s not ready at this time. That’s why they’re focusing on attacking America’s critical infrastructure vulnerabilities.
This is called an asymmetric response. They want to fight in the area where they can win or at least inflict enormous damage.
Look at all the crisis spots around the world. North Korea, the Persian Gulf, South China Sea, Syria. If any of them start to escalate, you’re going to get an asymmetric response function.
For example, if President Trump sends the Seventh Fleet into the South China Sea, China might unleash an attack of the U.S. power grid, creating chaos in the United States. Or it could launch an attack on the stock market or conduct other forms of financial warfare.
Financial warfare is not the warfare of the future — it is already here. It’s going to become a bigger threat as time goes on, too.
Financial warfare is actual warfare conducted through banking and capital markets channels. It is not mere economic policy as in the case of so-called currency wars, trade wars or embargoes.
When nations engage in financial warfare, individual investors can be collateral damage. If China tries to attack the U.S. by closing the New York Stock Exchange, for example, it will be tens of millions of Americans who will suffer an immediate loss of wealth as prices plunge and accounts are locked-down or frozen.
Financial warfare attacks vary in their degree of sophistication and impact. At the low end of the spectrum is a distributed denial of service, DDoS, attack. This is done by flooding a target server with an overwhelming volume of message traffic so that either the server shuts down or legitimate users cannot gain access. In such attacks, the target is not actually penetrated, but it is disabled by the message traffic jam.
The next level of sophistication is a cyberhack in which the target, say a bank account record file or a stock exchange order system, is actually penetrated. Once inside, the attacking cyberbrigade can either steal information, shut down the system or plant sleeper attack viruses that can be activated at a later date.
You have probably noticed that unexplained stock market outages and flash crashes have happened with increasing frequency.
Some of these events may be self-inflicted damage by the exchanges themselves in the course of software upgrades, but others are highly suspicious and the exact causes have never been disclosed by exchange officials.
But in 2010, the FBI and Department of Homeland Security located such an attack virus planted by Russian security services inside the Nasdaq stock market system.
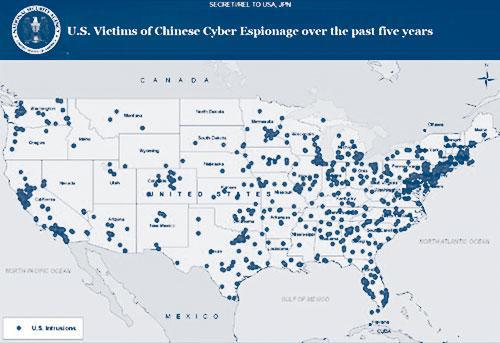
Here is a formerly classified map showing cyberattacks by the Chinese government against U.S. interests. Each dot represents an attack. Notice the concentration of attacks against technology targets in San Francisco, financial targets in New York and military and intelligence targets in the Washington-Virginia area.
The most dangerous attacks of all are those in which the enemy penetrates a bank or stock exchange not to disable it or steal information but to turn it into an enemy drone. Such a market drone can be used by attackers for maximum market disruption and the mass destruction of Americans’ wealth including your stocks and savings.
In this scenario, an attacker could penetrate the order entry system of a major stock exchange such as the New York Stock Exchange. Once inside the order entry system, the attacker would place large sell orders on highly liquid stocks such as Apple or Facebook.
Other system participants would then automatically match these orders in the mistaken belief that they were real trades. The sell orders would keep flooding the market and the selling pressure would feed on itself.
An attack of this type would be launched on a day when the market was already down 3% or more, about 550 points on the Dow Jones index.
The result could be a market decline of 20% or more in a single day, comparable to the stock market crash of October 1987 or the crash of 1929. You would not have to trade anything or be in the market during the attack; you would be wiped out based on the market decline even if you did nothing.
Another type of highly malicious attack is to penetrate the account records system of a major bank and then systematically erase account balances in customers’ deposit accounts and 401(k)s.
If the attack extended to backup databases, you or other customers might have no way of proving you ever owned the deleted accounts.
During a financial war game exercise at the Pentagon a few years back, I recommended that the SEC and New York Stock Exchange buy a warehouse in New York and equip it with copper wire hardline phones, hand-held battery powered calculators and other pre-Internet equipment. This facility would serve as a nondigital stock exchange with trading posts.
Orders would be phoned in on the hardwire analogue phone system. This is exactly how stocks were traded until recently. Computerized and algorithmic trading would be banned as nonessential.
In the event of a shutdown of the New York Stock Exchange by digital attack, the nondigital exchange would be activated. The U.S. would let China and Russia know this facility existed as a deterrent to a digital attack in the first place. If our rivals knew we had a robust nondigital Plan B, …read more
From:: Daily Reckoning